原文链接:https://devblogs.microsoft.com/oldnewthing/20040728-00/?p=38313
The “look” of the Windows user interface has gone through fashion cycles.
Windows 用户界面的『观感』经历了几轮时尚风格的更迭。
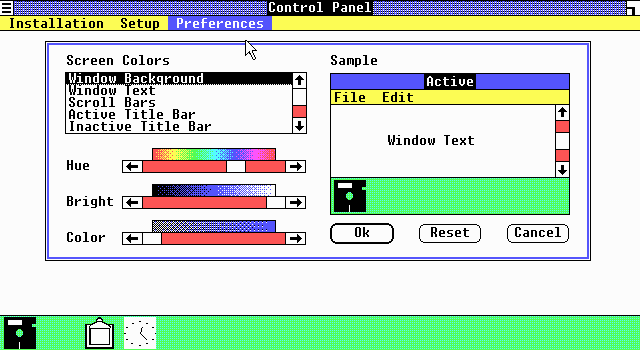
(译注:下文中的 Windows 1.0 截屏链接已失效,上图来自 ToastyTech)
In the beginning, there was Windows 1.0, which looked very flat because screen resolutions were rather low in those days and color depth was practically nonexistent. If you had 16 colors, you were doing pretty good. You couldn’t afford to spend very many pixels on fluff like borders, and shadows were out of the question due to lack of color depth.
一开始,是 Windows 1.0,那时候用户界面看上去非常平坦,因为那时的屏幕分辨率很低,并且色彩深度差不多还是不存在的东西。如果能用到16种色彩,就已经做得很不错了。你没有办法在例如边框这种小细节上浪费太多像素点,而阴影这种东西由于没有色彩深度,是完全不可能的事。
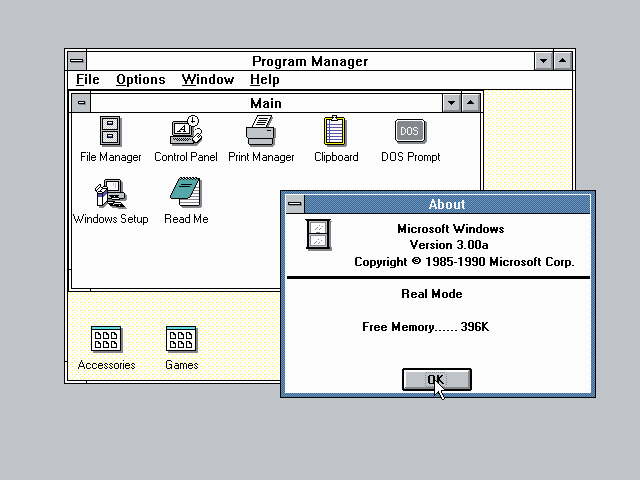
(译注:下文中的 Windows 3.0 截屏链接已失效,上图来自 ToastyTech)
The “flat look” continued in Windows 2.0, but Windows 3.0 added a hint of 3D (notice the beveling in the minimize/maximize buttons and in the toolbar buttons on the help window).
这种『平面观感』延续到了 Windows 2.0 中,不过到了Windows 3.0 增加了一丁点的 3D 效果(注意观察最小化、最大化按钮以及在帮助窗口的工具栏按钮上出现的斜边)。
Other people decided that the 3D look was the hot new thing, and libraries sprung up to add 3D shadow and outlining effects to nearly everything. The library CTL3D.DLL started out as just an Excel thing, but it grew in popularity until it became the “standard” way to make your dialog boxes “even more 3D”.
其它人感到这种 3D 效果在当时是热门的新事物,为几乎所有东西增加3D阴影和边线效果的库突然开始涌现。CTL3D.DLL 一开始只是 Excel 的一个组件,但却逐渐普及开来,直到最终成为了使对话框变得『更加3D』的标准方式。
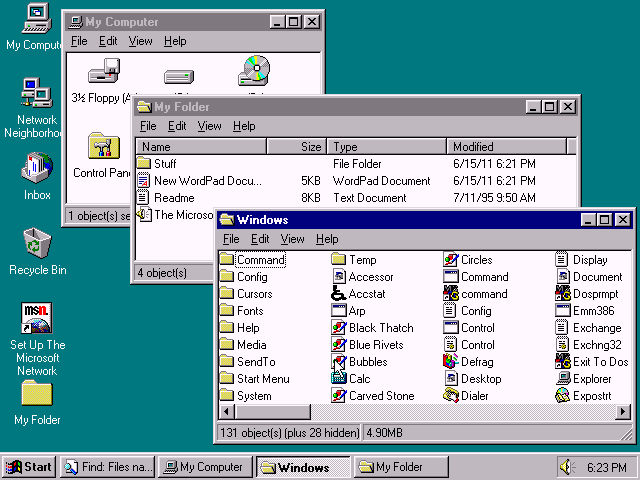
(译注:下文中的 Windows 95 截屏链接已失效,上图来自 ToastyTech)
Come Windows 95, even more of the system had a 3D look. Notice the beveling along the inside edge of the panes in the Explorer window. Furthermore, 3D-ness was turned on by default for all programs that marked themselves as “4.0”; i.e., programs that were designed for Windows 95. For programs that wanted to run on older versions of Windows as well, a new dialog style DS_3DLOOK was added, so that they could indicate that they wanted 3D-ization if available.
到了 Windows 95 的年代,系统中有越来越多的组件拥有了 3D 外观,可以注意观察资源管理器窗口中面板内角的斜边效果。此外,3D 效果对于将自己标记为『4.0』的——亦即为 Windows 95 而设计——的应用程序是默认开启的。至于那些仍然希望可以在旧版本 Windows 上运行的应用程序,系统为其增加了一种新的对话框样式:DS_3DLOOK,以便程序向系统提出其在可用时对其应用3D效果。
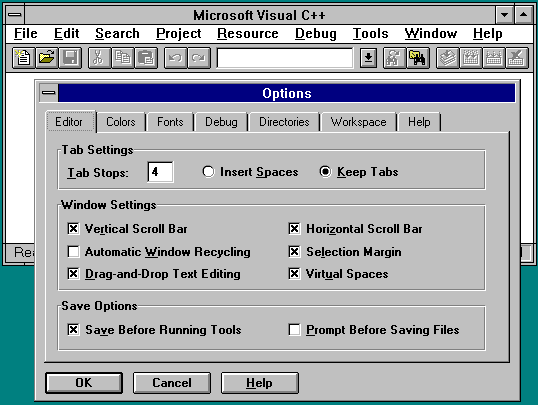
(译注:若读者不是从 Windows 3.x 年代过来的人,可能理解不了下文中『睫毛膏涂坏』的效果,上图为调用了CTL3D32.DLL 的对话框样例,截图来自 malSmith.net)
And if the 3D provided by Windows 95 by default wasn’t enough, you could use CTL3D32.DLL to make your controls even more 3D. By this point, things started getting really ugly. Buttons on dialog boxes had so many heavy black outlines that it started to look like a really bad mascara job.
如果 Windows 95 提供的 3D 效果还不够的话,你还可以调用 CTL3D32.DLL 来让你程序中的控件闲得更加 3D。至此,一切已经开始变得非常丑陋了。对话框中的按钮被添加了太多粗重的黑色边线,看上去就像把睫毛膏涂坏了一样。
Fortunately, like many fashions that get out of hand, people realized that too much 3D is not a good thing. User interfaces got flatter. Instead of using 3D effects and bold outlines to separate items, subtler dividers were used. Divider lines became more subdued and sometimes disappeared entirely.
幸运的是,就像那些失控的时尚潮流一样,人们开始意识到太多的 3D 效果并不是一件好事。用户界面(由此又)变得平面化起来。抛弃了运用 3D 效果和粗重的边线来划分窗体组件的做法,人们开始改用不易察觉的分隔线,而分隔线也变得越来越柔和,有时甚至完全消失了。
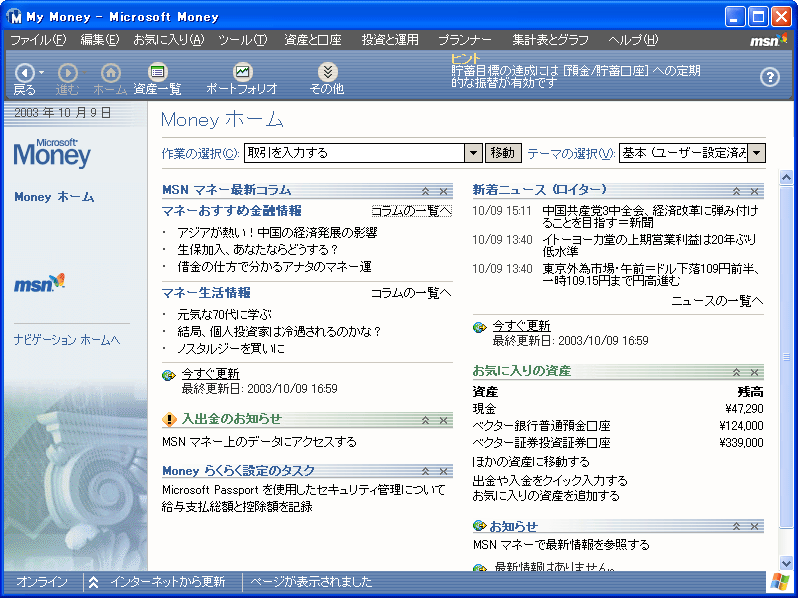
(译注:下文中的 Microsoft Money 截屏链接已失效,上图来自 Vector)
(译注:下文中的 Office 2000截屏链接已失效,上图来自 Wikipedia)
Microsoft Office and Microsoft Money were two programs that embraced the “less is more” approach. In this screenshot from Microsoft Money, observe that the beveling is gone. There are no 3D effects. Buttons are flat and unobtrusive. The task pane separates itself from the content pane by a simple gray line and a change in background shade. Even the toolbar has gone flat. Office 2000 also went largely flat, though some 3D effects linger, in the grooves and in the scrollbars (not visible in picture).
Microsoft Office 和 Microsoft Money 是两套拥抱『简单即为美』做法的应用程序。观察 Microsoft Money 的截屏,你会发现斜边效果不见了,3D 效果消失了,按钮变得平面化的同时也不再那么张扬了,任务面板通过划出一条简单的灰色直线、并改变其背景阴影的做法来将其与内容面板分隔开来,甚至工具栏都变『平』了。Office 2000 的界面也大范围变得平面化了,尽管在一些沟槽和滚动条上还是保留了一些 3D 效果(图中未展现)。
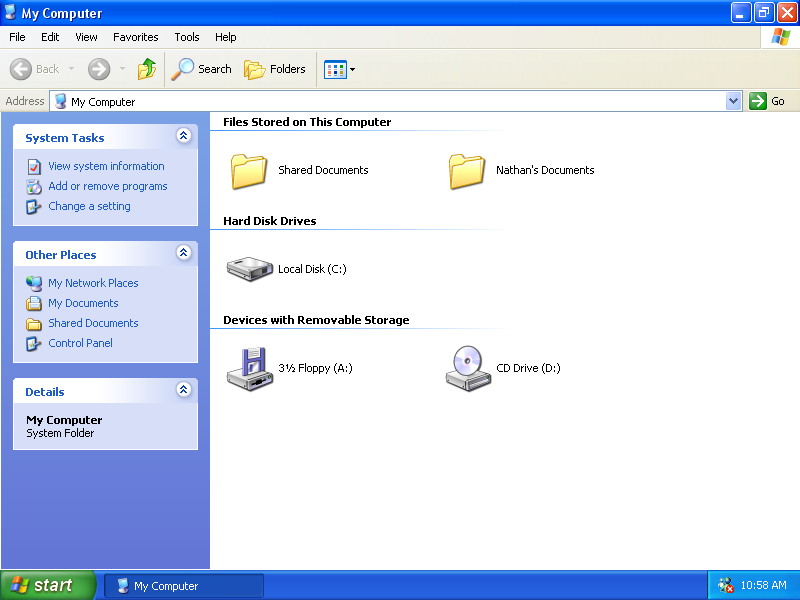
(译注:下文中的 Windows 95 截屏链接已失效,上图来自 ToastyTech)
Windows XP jumped on the “flat is good” bandwagon and even got rid of the separator line between the tasks pane and the contents pane. The division is merely implied by the change in color. “Separation through juxtaposition.”
Windows 追随了『平面即是美』的风尚,甚至将任务面板和内容面板(译注:大概指的是资源管理器左侧的信息栏和右边驱动器内容)之间的分隔线都给去掉了,二者之间仅仅用颜色的变化稍作分隔,即所谓的『以反差做分隔』。
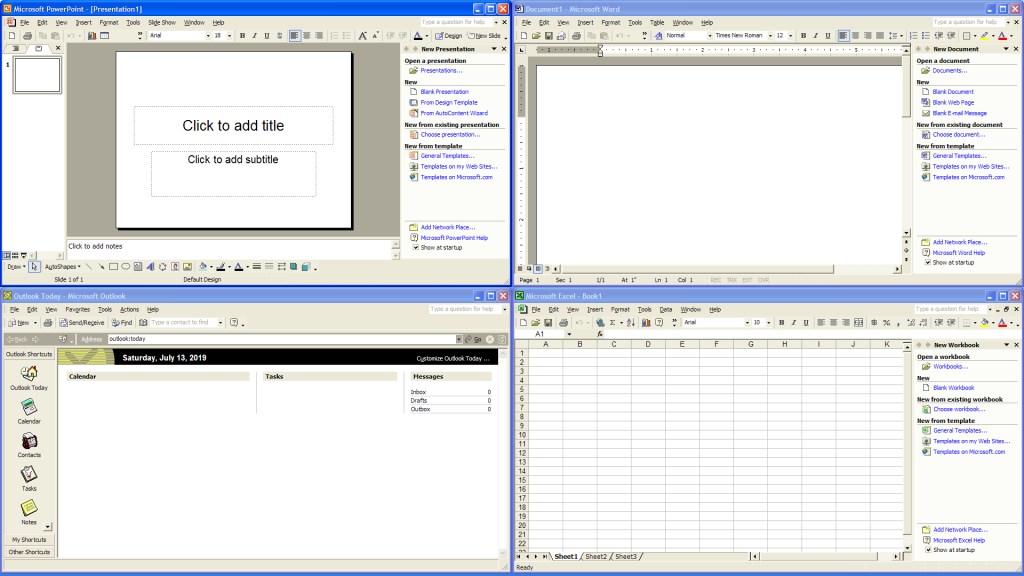
(译注:下文中的 Office XP 的截屏链接已失效,上图来自 Wikipedia)
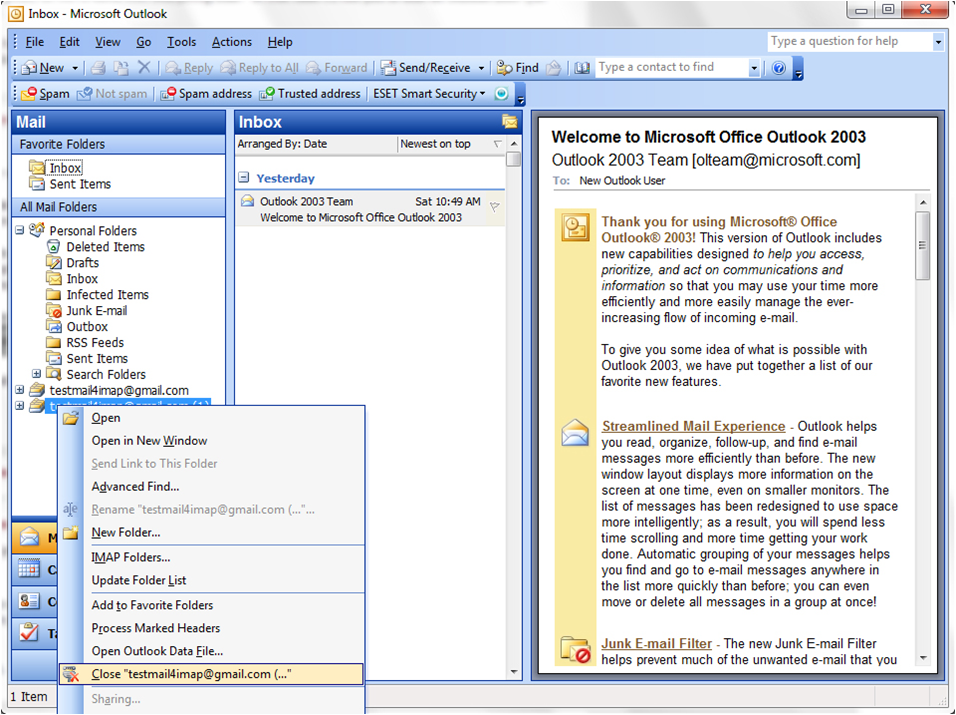
(译注:下文中的 Outlook 2003 的截屏链接已失效,上图来自 POP2IMAP.com)
Office XP and Outlook 2003 continue the trend and flatten nearly everything aside from the scrollbar elements. Blocks of color are used to separate elements onscreen, sometimes with the help of simple outlines.
Office XP 和 Outlook 2003 延续了这一趋势,并将除了滚动条之外的几乎所有组件都扁平化了。色块被用来分隔屏幕上的元素,有时也会附加简单的边线。
So now the pendulum of fashion has swung away from 3D back towards flatness. Who knows how long this school of visual expression will hold the upper hand. Will 3D return with a vengeance when people tire of the starkness of the flat look?
现在时尚的钟摆又从 3D 荡回了平面,谁也不知道这一风潮能占上风多久。等到人们厌倦了平面观感的时候,3D 会不会杀个回马枪呢?